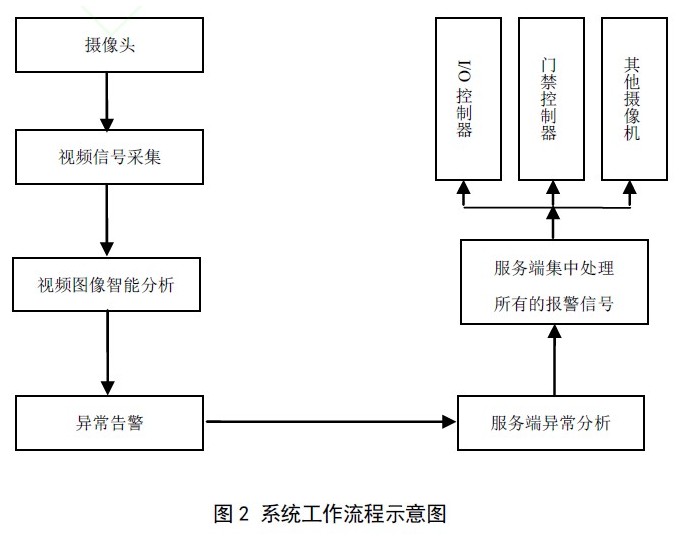
Abstract: Aiming at the problems that the current popular video surveillance system can not intelligently identify the surveillance target and can not intelligently handle the emergency situation, a security system design scheme based on intelligent video surveillance is proposed. The system is mainly composed of a monitoring terminal, a management terminal and a server. The network camera, infrared detection, electronic fence and other equipment are used to perform joint monitoring on the security area. The digital image analysis technology is used to detect the moving target in the monitoring scene in real time. Position, recognize, and understand behaviors, and intelligently control security areas. The paper focuses on the architecture design of intelligent video surveillance system and the realization of video intelligence analysis. 0 Preface With the continuous improvement of China's social economy, the public's awareness of security prevention is gradually improving, and video surveillance systems are increasingly being used in enterprises, schools, banks, and residential areas. However, at present, most video surveillance systems only provide real-time images to the staff, which are handled by manual monitoring. There are many shortcomings in this type of monitoring: First, most of these systems are unlikely to be configured with cameras and monitors in a 1:1 ratio, so most of the monitoring points cannot be monitored at all times; Second, some experiments have shown that if people continuously observe more than 2 monitors, they will miss 45% of the scene after 10 minutes, and after 22 minutes, they will miss 95% of the scenes, and the efficiency is extremely low. Third, since real-time supervision I can't see the psychological and physiological characteristics of people. In order not to miss the undiscovered situation, I have to make a 24-hour video recording for later reading. This produces a lot of useless information, a small amount of useful information is submerged in it, it is more difficult to obtain such useful information. Fourth, the business function is single, because it does not have intelligent analysis capabilities and linkage processing capabilities, it can only "monitor" And lack the ability to prevent "control" disposal. The intelligent video surveillance system uses artificial intelligence, pattern recognition, probability theory and image processing technology to analyze video data with the powerful data processing capabilities of the computer, filter out useless information or interference information in the image, extract key information from the video source, Determine if there are any abnormalities and handle them in the fastest and best way. The intelligent video surveillance system can effectively carry out pre-warning, handling in the event, and timely obtaining evidence afterwards. It is an intelligent system that is fully automatic, all-weather, and real-time monitoring. 1 Intelligent video surveillance system function analysis First, the intelligent video surveillance system can intelligently analyze the collected video data and implement various applications on the basis of the above. For example, when a target is detected to enter the monitoring area, the system automatically locks the target and performs tracking shooting. Video recording and simultaneous triggering of corresponding alarm linkage; face recognition and license plate recognition can be realized, and the entry and exit of personnel and vehicles can be intelligently recorded; combined with image fusion algorithm, the fusion of infrared light and visible light image can be realized, and the reliability of nighttime monitoring is enhanced. Secondly, the intelligent video surveillance system can effectively integrate other security equipment, such as access control systems, infrared detectors, smoke temperature probes, alarm bells, etc., to achieve integration and integration of security work, and give full play to the maximum efficiency of the system. For example, when the infrared detector finds that an unknown target enters the monitoring area, the system will promptly issue a command to request the corresponding network camera to go to the corresponding preset position, sound the alarm bell, and prompt the administrator to view the video signal of the road. This integrated system monitoring method is diverse, which can greatly reduce the false alarm rate and improve the efficiency of security work. Third, the intelligent video surveillance system can sense the working state of the front-end camera, such as video blur, video occlusion, video loss, and angle of view transformation. For example, in a large-scale monitoring system, there are usually hundreds or even thousands of monitoring points. The duty of the monitoring center can only monitor dozens of video images at most, when one of the videos is intentionally or unintentionally blocked. It is difficult for duty personnel to find out in time, which brings major security risks. The system has certain self-detection capabilities, which can detect and repair system problems in time and ensure the normal operation of the system. Fourth, the intelligent video surveillance system provides automatic evidence video retrieval for video recording. This function uses target detection technology to obtain the target type, shape, size, speed, position, color, and other specific target flag information to generate rich video. Indexing for specific video segment retrieval or target event retrieval. For example, enter "14:00 on August 23" to "16:00 on August 23" and walk through the "Blue Hat" personnel in the "6 kV distribution room". The system can find users based on these key information points. The related video has greatly improved the efficiency of video analysis. 2 Architecture design of intelligent video surveillance system 2.1 System Architecture Design The intelligent video surveillance system architecture proposed in this paper can be divided into two parts: software and hardware (as shown in Figure 1). The software part consists of four parts: system background monitoring terminal, management terminal, server and database; the hardware part mainly includes: network video camera, I/O electronic controller, various alarm sensors, searchlights, access control card reader, access controller Wait. 2.1.1 Software component (1) Monitoring terminal: It is the information processing unit of the intelligent video monitoring system. It is responsible for connecting the user and the central server. It is the relay station for information and the key to ensuring that the user can receive video information and alarms in the first time. Its main functions are: viewing real-time monitoring images, receiving alarm prompts, querying historical alarm records, and remotely operating various types of alarm devices. (2) Management terminal: mainly used for personnel authority configuration, hardware device configuration, system linkage alarm program setting, timing plan management. (3) Server: As the nerve center of the intelligent video surveillance system, it bears many duties such as hardware device management, data communication, historical video recording management, network congestion control, and alarm intelligent processing. In order to ensure the security, stability and ease of use of the system, the monitoring terminal, management terminal and server are written in C# language and run on Microsoft's WINODWS operating system. (4) Database: It adopts Microsoft's SQL2005 database, which has excellent performance, relatively simple operation and high security. All hardware information, personnel information, alarm handling plan, alarm history record, and video index in the system are stored here, which is convenient for modification and call. 2.1.2 Hardware components (1) Network camera: It consists of lens, image/sound collector, digital image/sound encoder, network control server and so on. It has a built-in storage device such as an SD card and has a certain storage capacity; the image video/audio output signal quality is good, and supports the popular M-JPEG/H.264 codec. The most important thing is that the network camera has a built-in processor, which can realize the target recognition, extraction, classification and behavior analysis of video images by means of advanced image analysis algorithms. Once an abnormal situation is detected, it can be sent to the system server through the network. Alarm information. (2) I/O controller: the input and output controller, which can receive and convert electrical signals from other devices, and can also send appropriate electrical signal sequences to these devices; it has a network communication interface. Supports common network communication protocols such as TCP/IP, and can exchange information with other devices through the network; has a certain capacity of alarm data storage function, can record alarm information locally when the network is not smooth; interface is rich, with RS-232 Communication interfaces such as /RS-485 are compatible with common alarm devices on the market. (3) Access controller: It has a built-in card number database to support local card verification; it can open and close the door remotely; when the access controller has an unexpected situation, it can send an alarm signal to the user. (4) All kinds of alarm equipment, such as electronic fences, infrared detectors, fire detectors, auxiliary lighting, alarm buttons, etc. 2.2 System Workflow The system workflow is shown in Figure 2. After the front-end camera captures the video signal, the built-in embedded processor directly performs digital image analysis to extract valuable targets. Analyze and judge the shape and behavior trend of the device. If it is determined that an abnormal situation occurs, it will send relevant abnormal alarm information to the server. The server will refer to the user's preset alarm rules to analyze the abnormal alarm in detail. The preset alarm condition, the system sends an alarm message to the staff, and sends a control command to the relevant I/O controller and the access controller according to the preset alarm handling scheme to perform safety control. The purpose of the system preset alarm rule is to be as accurate as possible in order to be able to analyze the abnormal state of the monitoring location in various environments, and to reduce the occurrence of false negatives and false positives. To this end, first of all, according to the type of environment in which the monitoring system is located, the scenes set by the early warning are divided into four categories: indoor, outdoor, day and night. The targets to be monitored can be divided into people, motor vehicles, non-motor vehicles and animals. Several major categories. Secondly, after completing the setting of the on-site environment type and the early warning target, the monitored area should be divided into specific warning types such as warning area, non-alert area and monitoring area. The combination of the alert type and the target type can give full play to the advantages of the intelligent video surveillance system in signal acquisition and data processing. In different environments, for different types of alert, according to different actual situations, timely and accurate Early warning, thus effectively improving the pertinence and accuracy of early warning. Relevant information: Security System Design Based on Intelligent Video Surveillance (2)
Lanejoy is all kinds of spring Manufacturer at china 10 years, we had made compression spring, Wire Spring, Torsion Spring, Tension Spring, recoil spring and so on.
we also can do for OEM OR ODM
compression spring,wire spring,torsion spring,tension spring,recoil spring Shenzhen Lanejoy Technology Co.,LTD , https://www.szsmallcompressionspring.com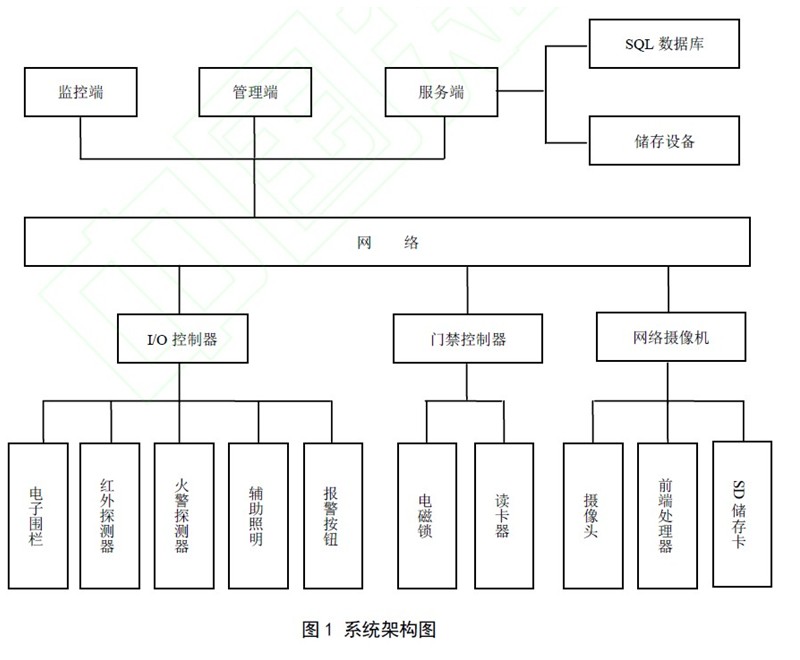
Security System Design Based on Intelligent Video Surveillance (1)
0 times
Window._bd_share_config = { "common": { "bdSnsKey": {}, "bdText": "", "bdMini": "2", "bdMiniList": false, "bdPic": "", "bdStyle": " 0", "bdSize": "24" }, "share": {}, "image": { "viewList": ["qzone", "tsina", "tqq", "renren", "weixin"], "viewText": "Share to:", "viewSize": "16" }, "selectShare": { "bdContainerClass": null, "bdSelectMiniList": ["qzone", "tsina", "tqq", "renren" , "weixin"] } }; with (document) 0[(getElementsByTagName('head')[0] || body).appendChild(createElement('script')).src = 'http://bdimg.share. Baidu.com/static/api/js/share.js?v=89860593.js?cdnversion=' + ~(-new Date() / 36e5)];
